Fuzzing exiftags
Write a harness
int
main(int argc, char **argv)
{
register int ch;
int dumplvl, pas, eval;
char *mode;
FILE *fp;
progname = argv[0];
dumplvl = eval = 0;
debug = quiet = FALSE;
pas = TRUE;
#ifdef WIN32
mode = "rb";
#else
mode = "r";
#endif
while ((ch = getopt(argc, argv, "acivuldqs:")) != -1)
switch (ch) {
case 'a':
dumplvl |= (ED_CAM | ED_IMG | ED_VRB);
break;
case 'c':
dumplvl |= ED_CAM;
break;
case 'i':
dumplvl |= ED_IMG;
break;
case 'v':
dumplvl |= ED_VRB;
break;
case 'u':
dumplvl |= ED_UNK;
break;
case 'l':
pas = FALSE;
break;
case 'd':
debug = TRUE;
break;
case 'q':
quiet = TRUE;
break;
case 's':
delim = optarg;
break;
case '?':
default:
usage();
}
argc -= optind;
argv += optind;
if (!dumplvl && !debug)
dumplvl |= (ED_CAM | ED_IMG);
if (debug && (dumplvl & ED_UNK))
dumplvl |= ED_BAD;
#ifdef __AFL_HAVE_MANUAL_CONTROL
__AFL_INIT();
#endif
while (__AFL_LOOP(1000)) {
fp = fopen(*argv, mode);
if (doit(fp, dumplvl, pas))
eval = 1;
fclose(fp);
}
exit(eval);
}
Result
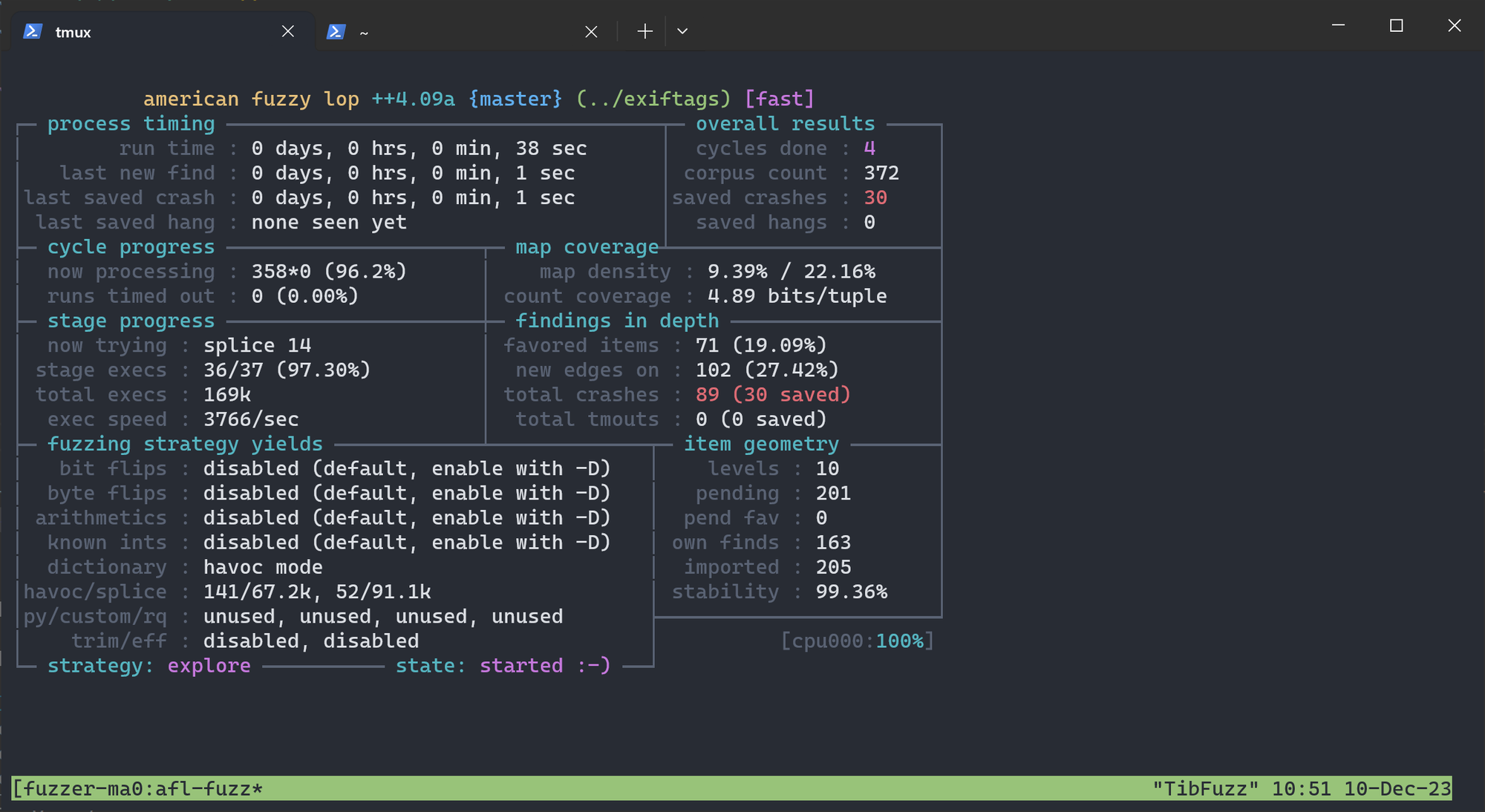
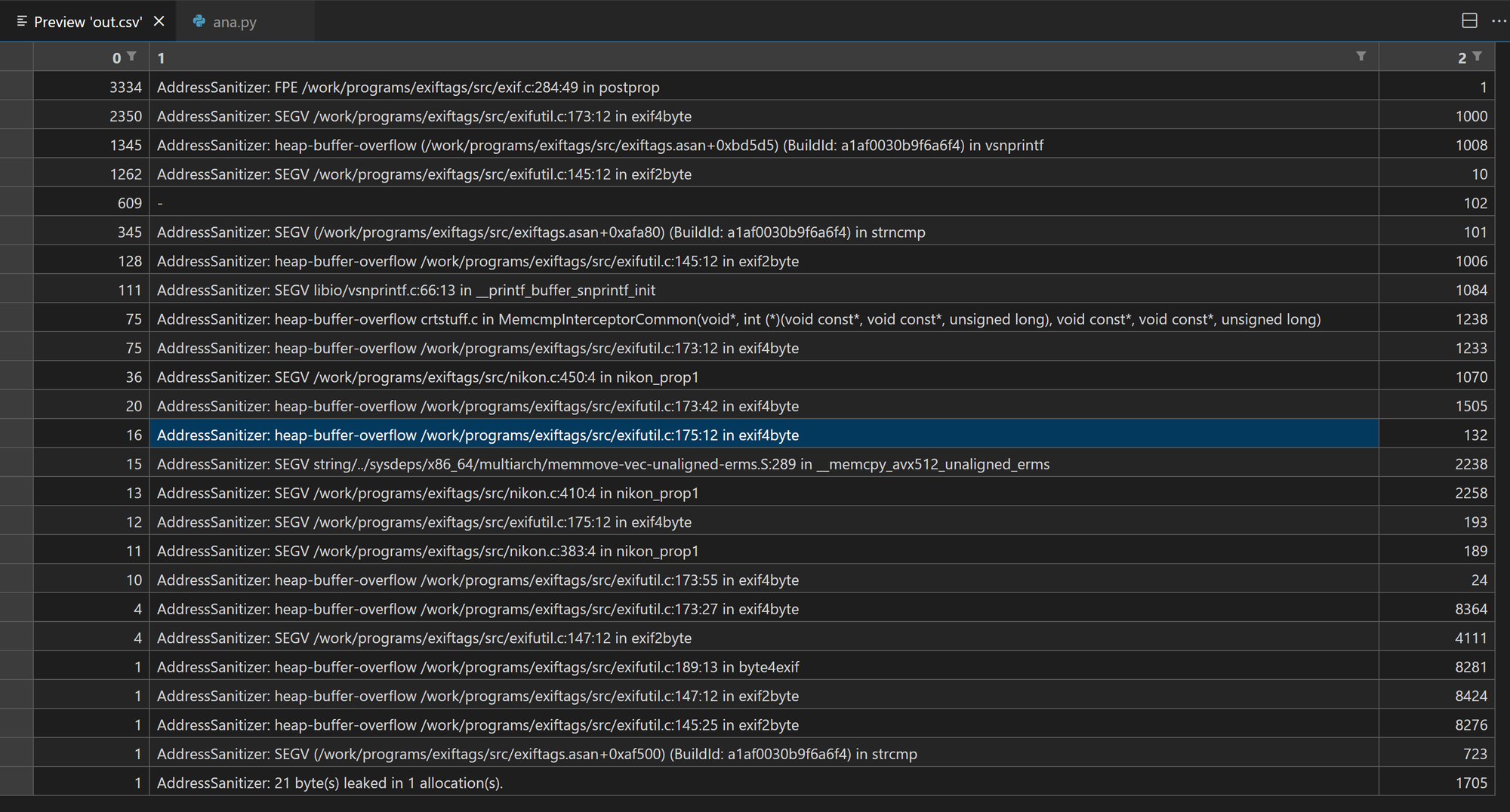
After one day, thousands of crash cases have been collected.
Reproduce
To exploit, user need to run:
# Tested on Debian 12, 2023/12/10
apt install exiftags
exiftags sample.jpeg
Samples & ASan report download: sample_exiftags.zip
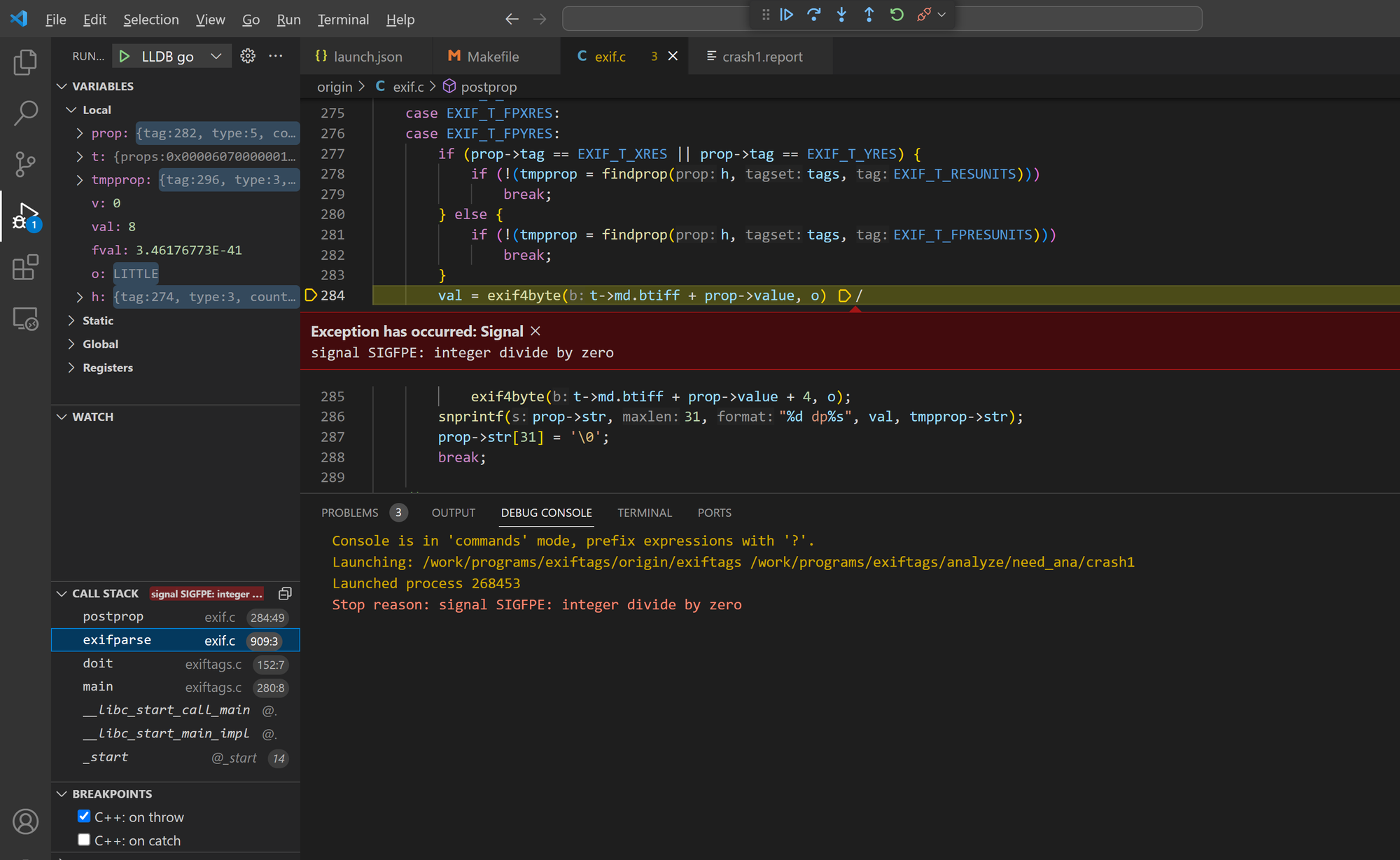
Bug 1 - division by zero in postprop()
The postprop() function in Exiftags 1.01 has a division by zero error, potentially leading to a Denial of Service.
Sample files: crash1
AddressSanitizer:DEADLYSIGNAL
=================================================================
==235938==ERROR: AddressSanitizer: FPE on unknown address 0x559c5e7f84ba (pc 0x559c5e7f84ba bp 0x7ffe38783bc0 sp 0x7ffe38783a40 T0)
#0 0x559c5e7f84ba in postprop /work/programs/exiftags/src/exif.c:284:49
#1 0x559c5e7f84ba in exifparse /work/programs/exiftags/src/exif.c:909:3
#2 0x559c5e7f84ba in doit /work/programs/exiftags/src/exiftags.c:152:7
#3 0x559c5e7f5c80 in main /work/programs/exiftags/src/exiftags.c:280:8
#4 0x7f616a42a6c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#5 0x7f616a42a784 in __libc_start_main csu/../csu/libc-start.c:360:3
#6 0x559c5e71afd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: FPE /work/programs/exiftags/src/exif.c:284:49 in postprop
==235938==ABORTING
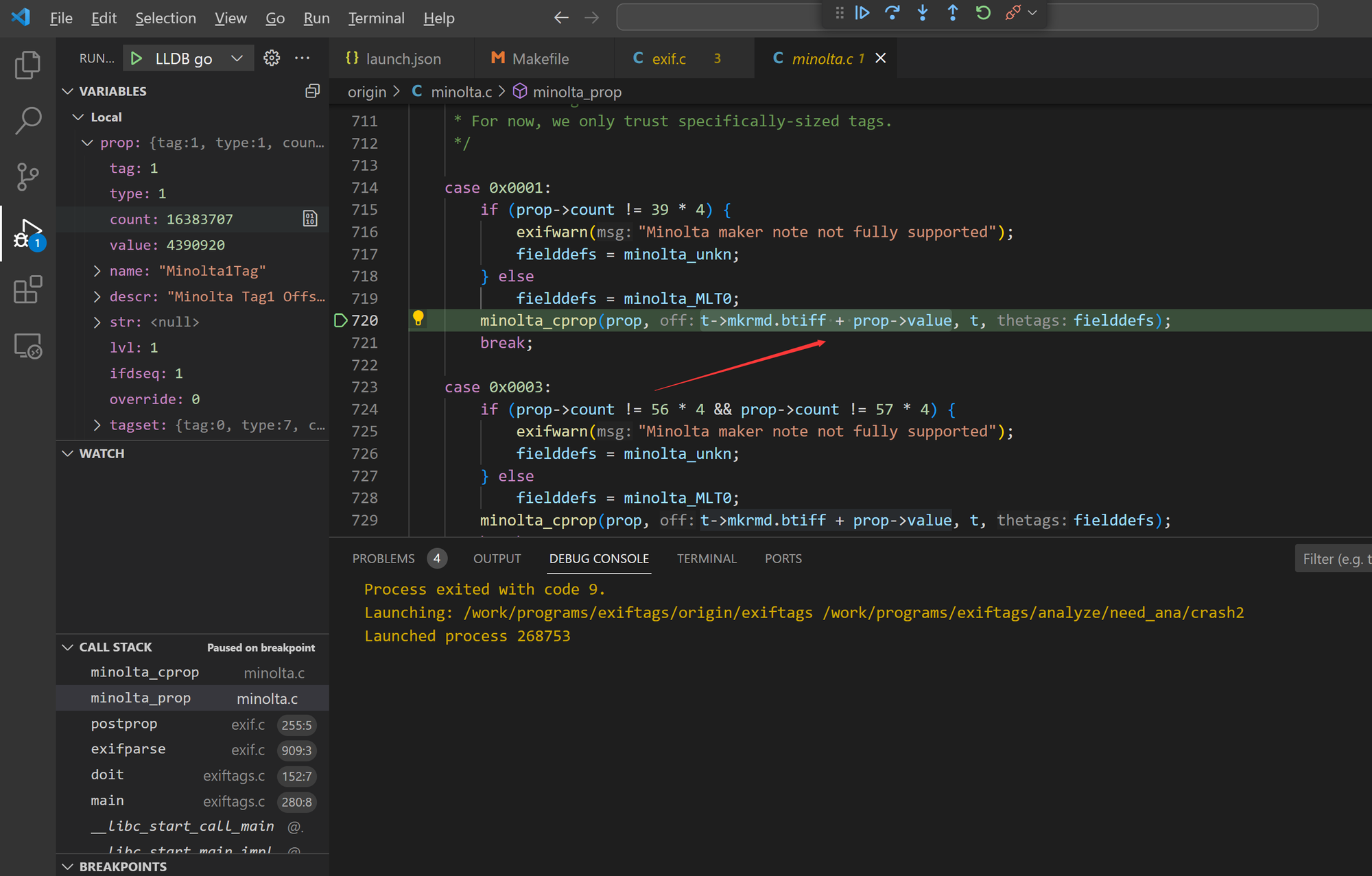
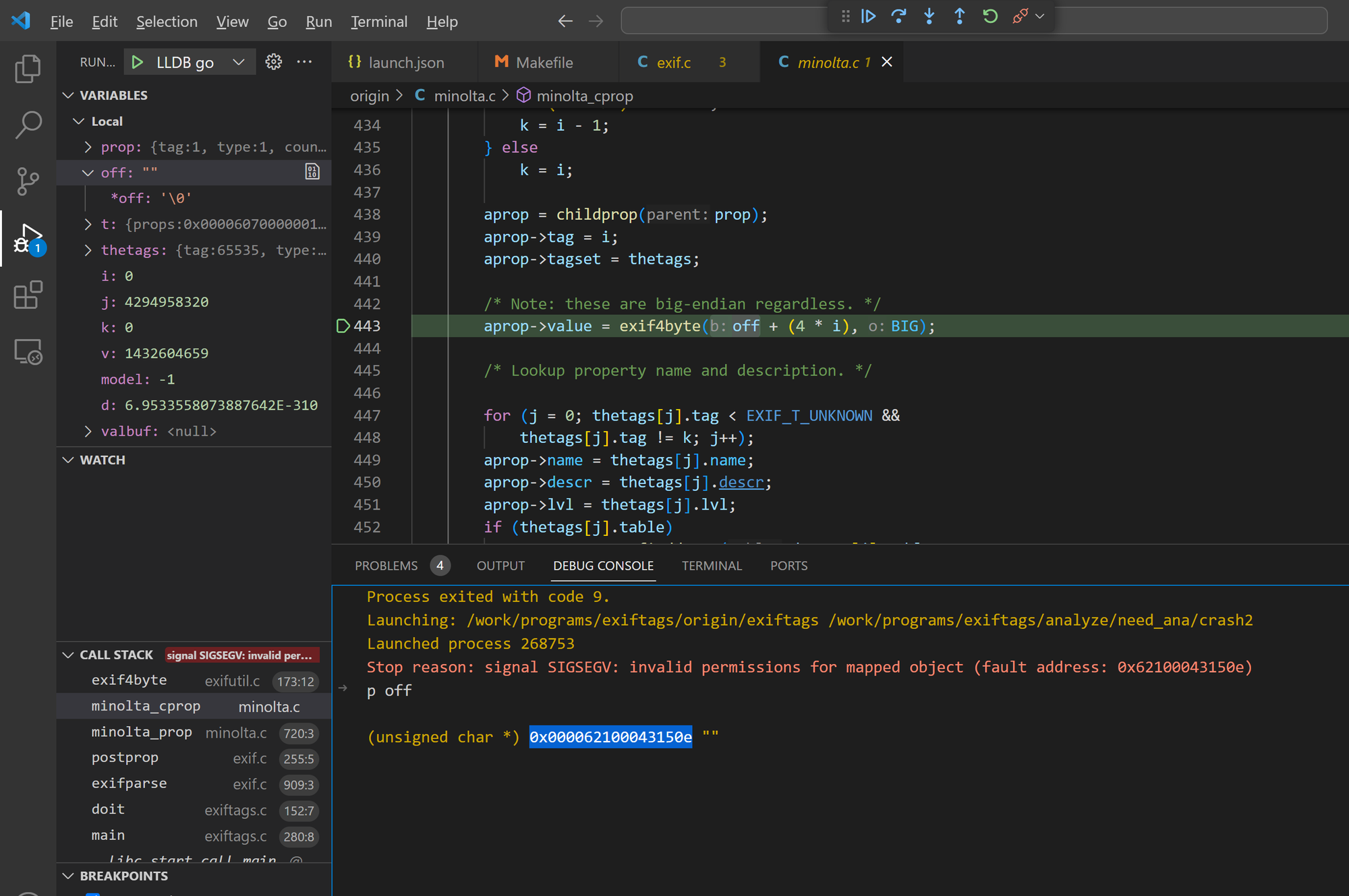
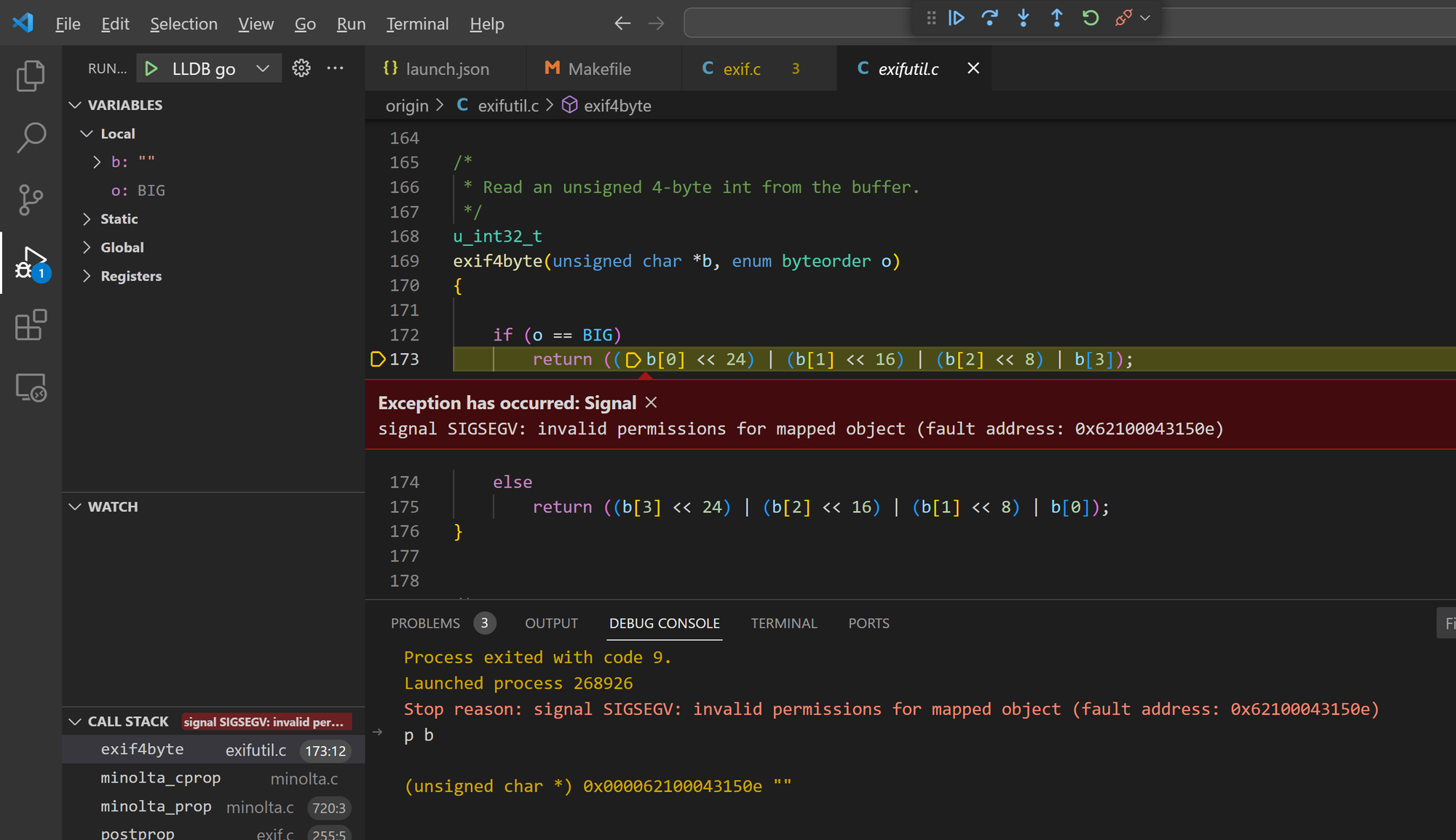
Bug 2 - arbitary memory read in minolta_prop()
The minolta_prop() function in Exiftags 1.01 has an offset field overflow issue, leading to arbitrary address reads.
Sample files: crash2, crash12, crash19, crash21
AddressSanitizer:DEADLYSIGNAL
=================================================================
==253611==ERROR: AddressSanitizer: SEGV on unknown address 0x62100043150e (pc 0x55a25599fffd bp 0x7ffd0c1e2d30 sp 0x7ffd0c1e2c10 T0)
==253611==The signal is caused by a READ memory access.
#0 0x55a25599fffd in exif4byte /work/programs/exiftags/src/exifutil.c:173:12
#1 0x55a2559b3a17 in minolta_cprop /work/programs/exiftags/src/minolta.c:443:18
#2 0x55a2559b6161 in minolta_prop /work/programs/exiftags/src/minolta.c
#3 0x55a25599376d in postprop /work/programs/exiftags/src/exif.c:255:5
#4 0x55a25599376d in exifparse /work/programs/exiftags/src/exif.c:909:3
#5 0x55a25599376d in doit /work/programs/exiftags/src/exiftags.c:152:7
#6 0x55a255991c80 in main /work/programs/exiftags/src/exiftags.c:280:8
#7 0x7f88fdb976c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#8 0x7f88fdb97784 in __libc_start_main csu/../csu/libc-start.c:360:3
#9 0x55a2558b6fd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /work/programs/exiftags/src/exifutil.c:173:12 in exif4byte
==253611==ABORTING
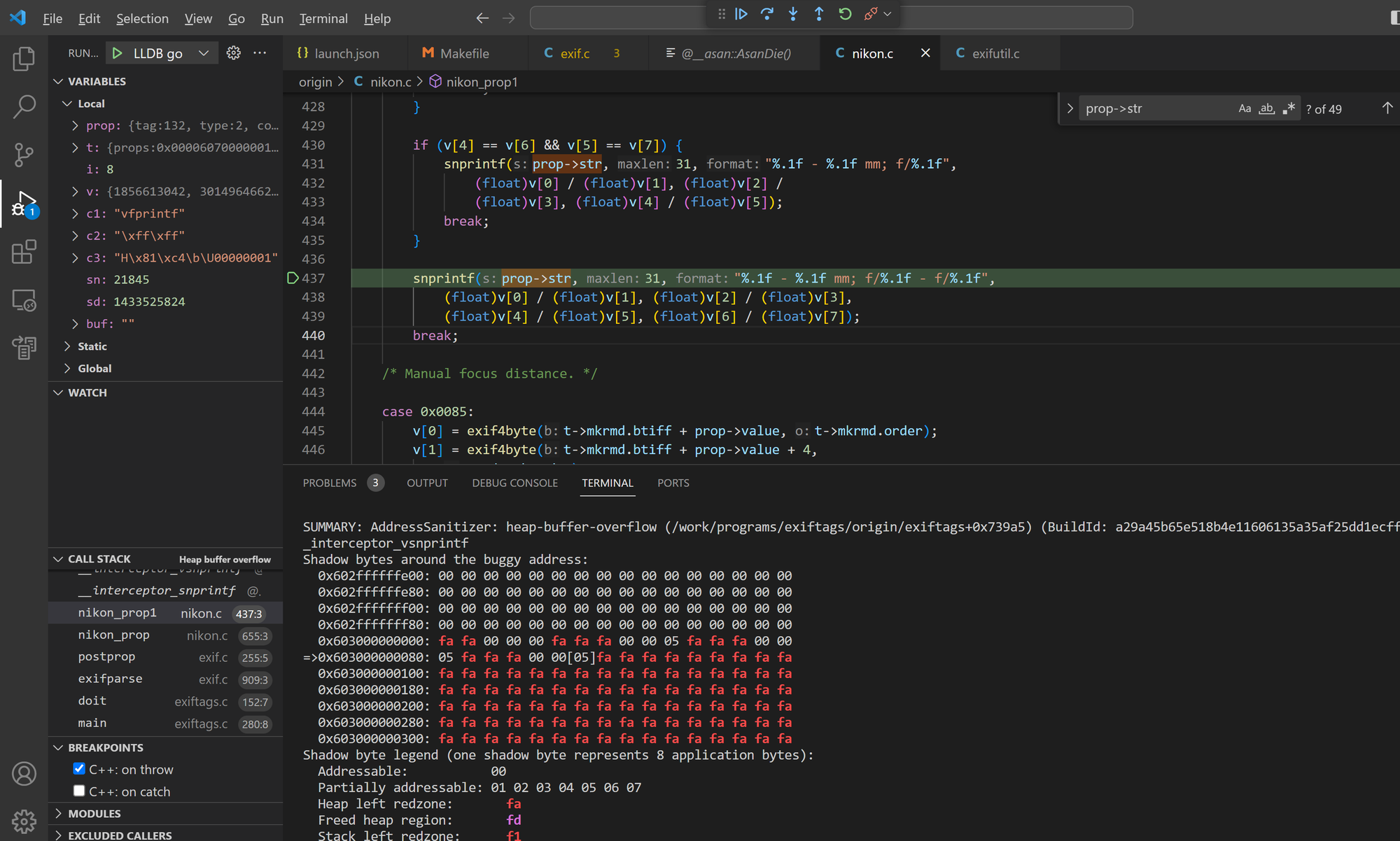
Bug 3 - heap buffer overflow in nikon_prop1()
The nikon_prop1() function in Exiftags 1.01 has a heap overflow vulnerability where snprintf() can write to an illegal address.
Sample files: crash3, crash13
=================================================================
==238558==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6030000000b5 at pc 0x55f218a415d6 bp 0x7ffd85371b80 sp 0x7ffd85371320
WRITE of size 28 at 0x6030000000b5 thread T0
#0 0x55f218a415d5 in vsnprintf (/work/programs/exiftags/src/exiftags.asan+0xbd5d5) (BuildId: a1af0030b9f6a6f4)
#1 0x55f218a42ed4 in snprintf (/work/programs/exiftags/src/exiftags.asan+0xbeed4) (BuildId: a1af0030b9f6a6f4)
#2 0x55f218b1503e in nikon_prop1 /work/programs/exiftags/src/nikon.c:437:3
#3 0x55f218b1503e in nikon_prop /work/programs/exiftags/src/nikon.c:655:3
#4 0x55f218af876d in postprop /work/programs/exiftags/src/exif.c:255:5
#5 0x55f218af876d in exifparse /work/programs/exiftags/src/exif.c:909:3
#6 0x55f218af876d in doit /work/programs/exiftags/src/exiftags.c:152:7
#7 0x55f218af6c80 in main /work/programs/exiftags/src/exiftags.c:280:8
#8 0x7fa2935286c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#9 0x7fa293528784 in __libc_start_main csu/../csu/libc-start.c:360:3
#10 0x55f218a1bfd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
0x6030000000b5 is located 0 bytes after 21-byte region [0x6030000000a0,0x6030000000b5)
allocated by thread T0 here:
#0 0x55f218ab6e1c in calloc (/work/programs/exiftags/src/exiftags.asan+0x132e1c) (BuildId: a1af0030b9f6a6f4)
#1 0x55f218b0693e in exifstralloc /work/programs/exiftags/src/exifutil.c:327:23
#2 0x55f218af7f28 in exifparse /work/programs/exiftags/src/exif.c:902:12
#3 0x55f218af7f28 in doit /work/programs/exiftags/src/exiftags.c:152:7
#4 0x55f218af6c80 in main /work/programs/exiftags/src/exiftags.c:280:8
SUMMARY: AddressSanitizer: heap-buffer-overflow (/work/programs/exiftags/src/exiftags.asan+0xbd5d5) (BuildId: a1af0030b9f6a6f4) in vsnprintf
Shadow bytes around the buggy address:
0x602ffffffe00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x602ffffffe80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x602fffffff00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x602fffffff80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x603000000000: fa fa 00 00 00 fa fa fa 00 00 05 fa fa fa 00 00
=>0x603000000080: 05 fa fa fa 00 00[05]fa fa fa fa fa fa fa fa fa
0x603000000100: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x603000000180: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x603000000200: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x603000000280: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x603000000300: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==238558==ABORTING
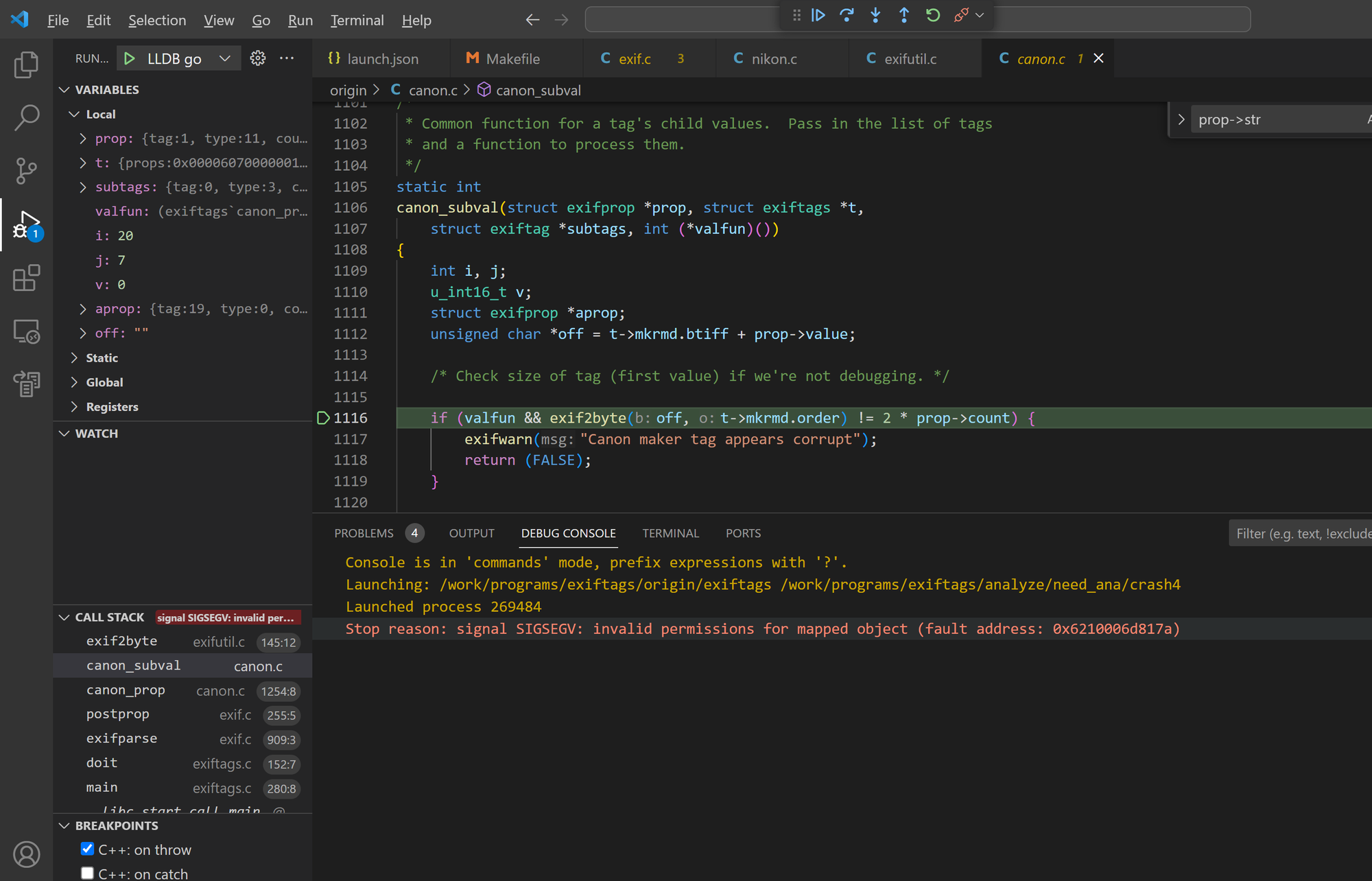
Bug 4 - arbitary memory read in canon_subval()
The canon_subval() function in Exiftags 1.01 has an arbitrary address read issue.
Sample files: crash4, crash7, crash20, crash23, crash24
AddressSanitizer:DEADLYSIGNAL
=================================================================
==235253==ERROR: AddressSanitizer: SEGV on unknown address 0x6210006d817a (pc 0x5623e2512db9 bp 0x7fff12948480 sp 0x7fff12948220 T0)
==235253==The signal is caused by a READ memory access.
#0 0x5623e2512db9 in exif2byte /work/programs/exiftags/src/exifutil.c:145:12
#1 0x5623e251c7ad in canon_subval /work/programs/exiftags/src/canon.c:1116:16
#2 0x5623e2519b45 in canon_prop /work/programs/exiftags/src/canon.c:1254:8
#3 0x5623e250676d in postprop /work/programs/exiftags/src/exif.c:255:5
#4 0x5623e250676d in exifparse /work/programs/exiftags/src/exif.c:909:3
#5 0x5623e250676d in doit /work/programs/exiftags/src/exiftags.c:152:7
#6 0x5623e2504c80 in main /work/programs/exiftags/src/exiftags.c:280:8
#7 0x7fd3db71e6c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#8 0x7fd3db71e784 in __libc_start_main csu/../csu/libc-start.c:360:3
#9 0x5623e2429fd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /work/programs/exiftags/src/exifutil.c:145:12 in exif2byte
==235253==ABORTING
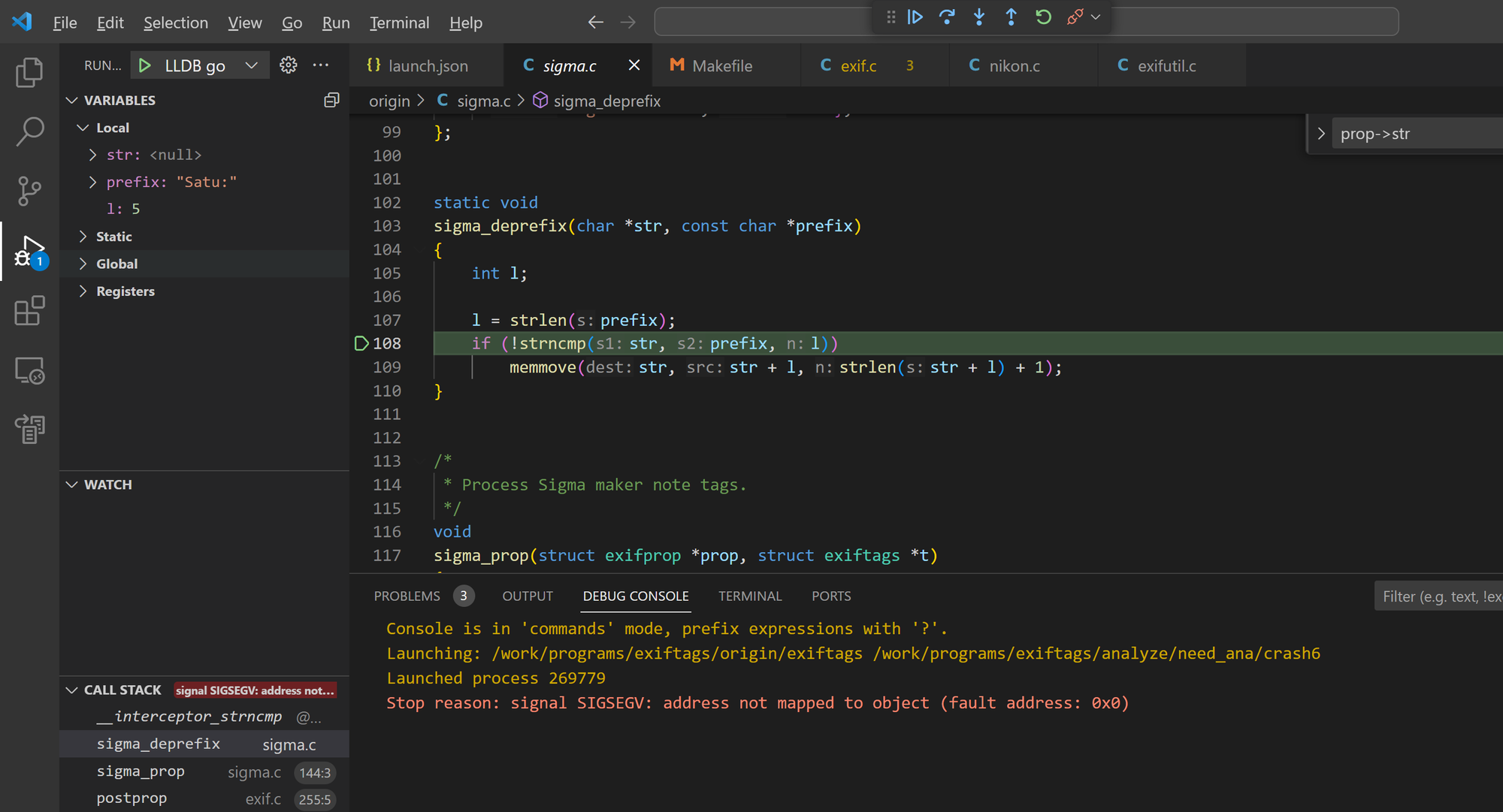
Bug 5 - null pointer dereference in sigma_deprefix()
The sigma_deprefix() function in Exiftags 1.01 has a null pointer dereference issue, leading to illegal memory access.
Sample files: crash6
AddressSanitizer:DEADLYSIGNAL
=================================================================
==232476==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55cd4c8bfa80 bp 0x7ffccab2d150 sp 0x7ffccab2c8f0 T0)
==232476==The signal is caused by a READ memory access.
==232476==Hint: address points to the zero page.
#0 0x55cd4c8bfa80 in strncmp (/work/programs/exiftags/src/exiftags.asan+0xafa80) (BuildId: a1af0030b9f6a6f4)
#1 0x55cd4c9adc7e in sigma_deprefix /work/programs/exiftags/src/sigma.c:108:7
#2 0x55cd4c9adc7e in sigma_prop /work/programs/exiftags/src/sigma.c:144:3
#3 0x55cd4c98476d in postprop /work/programs/exiftags/src/exif.c:255:5
#4 0x55cd4c98476d in exifparse /work/programs/exiftags/src/exif.c:909:3
#5 0x55cd4c98476d in doit /work/programs/exiftags/src/exiftags.c:152:7
#6 0x55cd4c982c80 in main /work/programs/exiftags/src/exiftags.c:280:8
#7 0x7fee9ef1d6c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#8 0x7fee9ef1d784 in __libc_start_main csu/../csu/libc-start.c:360:3
#9 0x55cd4c8a7fd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (/work/programs/exiftags/src/exiftags.asan+0xafa80) (BuildId: a1af0030b9f6a6f4) in strncmp
==232476==ABORTING
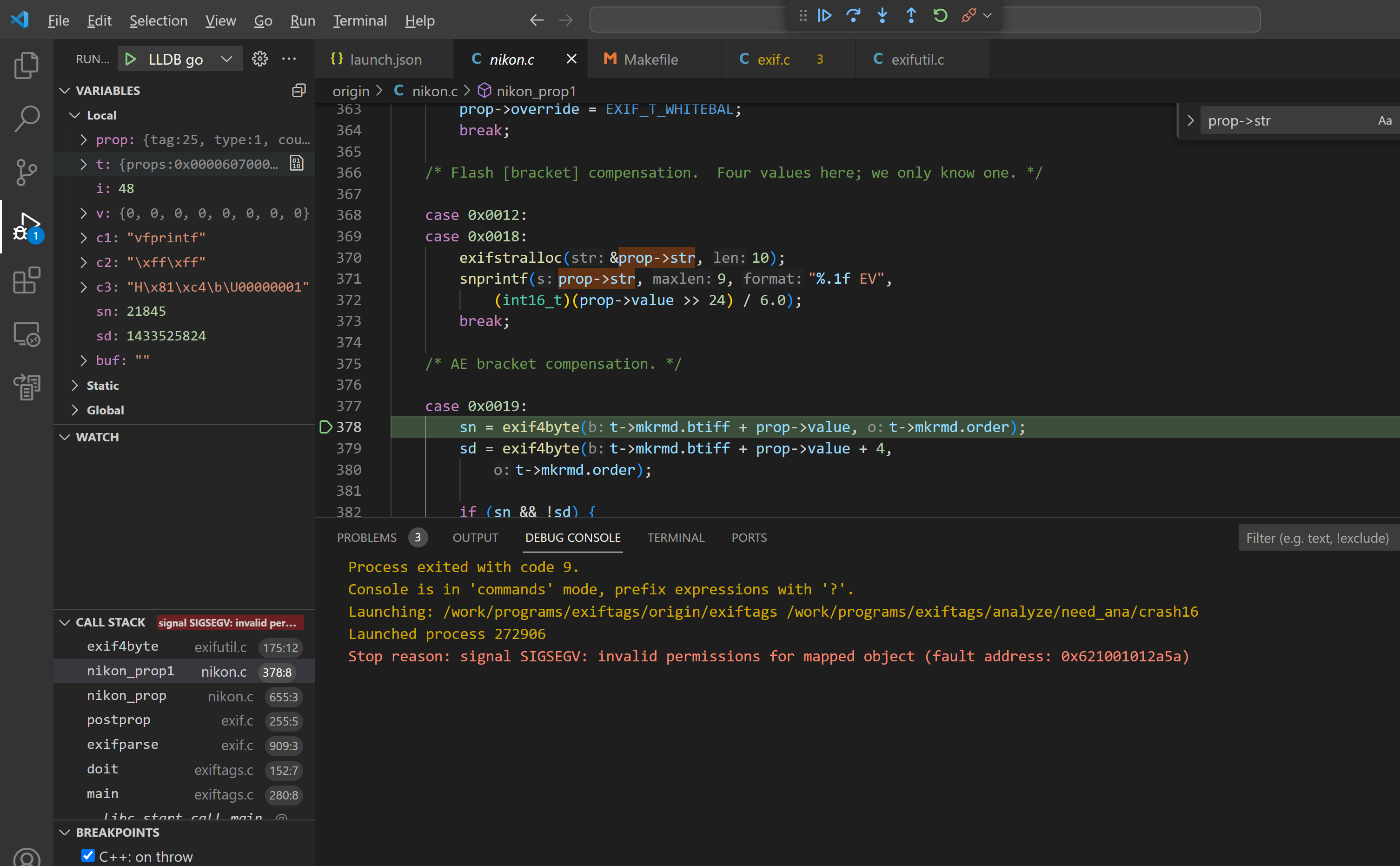
Bug 6 - arbitary memory read & nullptr dereference in nikon_prop1()
The nikon_prop1() function in Exiftags 1.01 has an offset field overflow issue, leading to arbitrary address reads.
Sample files: crash8, crash11, crash15, crash16, crash17
AddressSanitizer:DEADLYSIGNAL
=================================================================
==235948==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f5f2285c370 bp 0x7ffe6630bfc0 sp 0x7ffe6630b6a0 T0)
==235948==The signal is caused by a WRITE memory access.
==235948==Hint: address points to the zero page.
#0 0x7f5f2285c370 in __printf_buffer_snprintf_init libio/vsnprintf.c:66:13
#1 0x7f5f2285c370 in __vsnprintf_internal libio/vsnprintf.c:95:3
#2 0x7f5f2285c370 in vsnprintf libio/vsnprintf.c:103:10
#3 0x5559ed58540f in vsnprintf (/work/programs/exiftags/src/exiftags.asan+0xbd40f) (BuildId: a1af0030b9f6a6f4)
#4 0x5559ed586ed4 in snprintf (/work/programs/exiftags/src/exiftags.asan+0xbeed4) (BuildId: a1af0030b9f6a6f4)
#5 0x5559ed658b80 in nikon_prop1 /work/programs/exiftags/src/nikon.c
#6 0x5559ed658b80 in nikon_prop /work/programs/exiftags/src/nikon.c:655:3
#7 0x5559ed63c76d in postprop /work/programs/exiftags/src/exif.c:255:5
#8 0x5559ed63c76d in exifparse /work/programs/exiftags/src/exif.c:909:3
#9 0x5559ed63c76d in doit /work/programs/exiftags/src/exiftags.c:152:7
#10 0x5559ed63ac80 in main /work/programs/exiftags/src/exiftags.c:280:8
#11 0x7f5f228066c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#12 0x7f5f22806784 in __libc_start_main csu/../csu/libc-start.c:360:3
#13 0x5559ed55ffd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV libio/vsnprintf.c:66:13 in __printf_buffer_snprintf_init
==235948==ABORTING
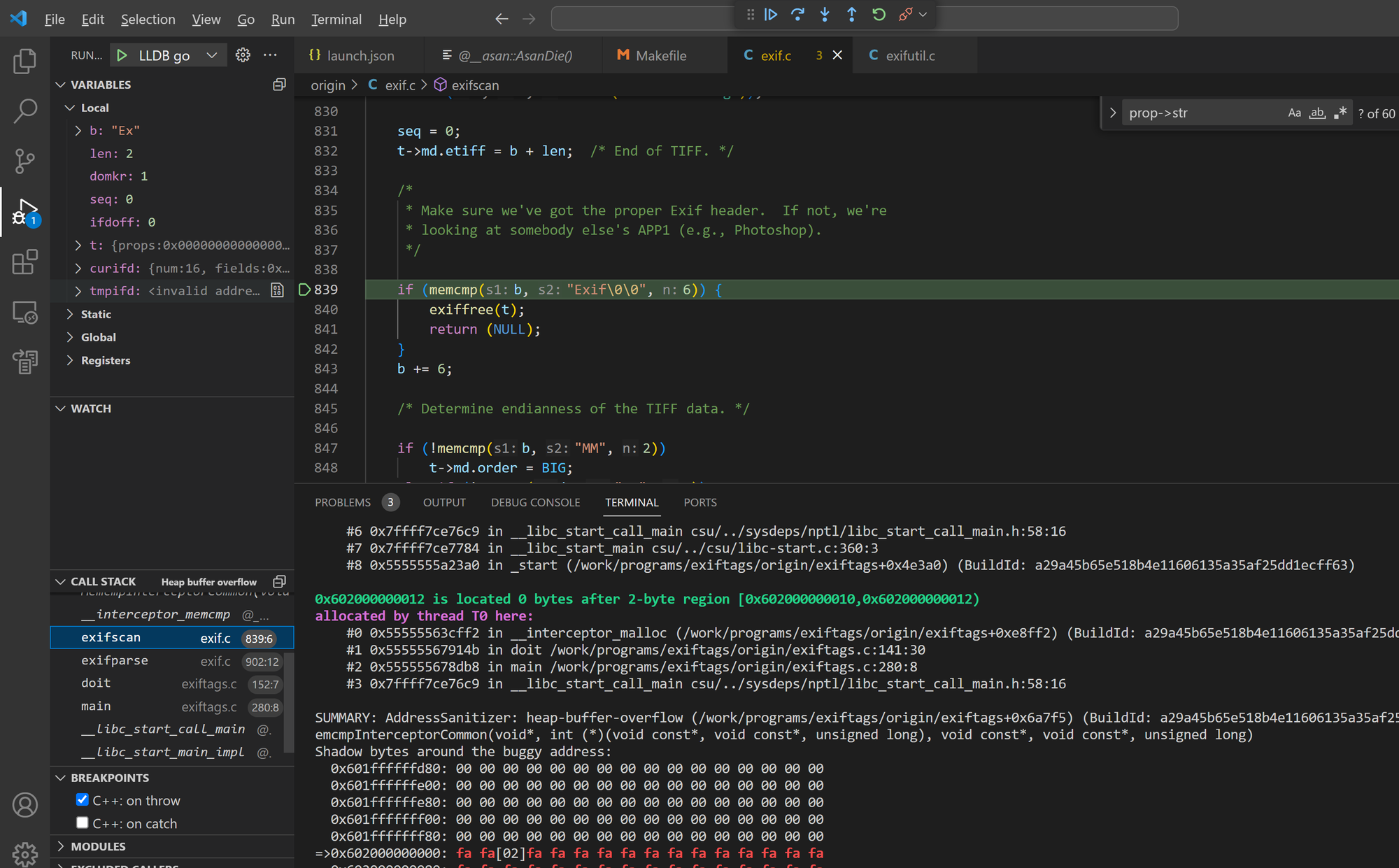
Bug 7 - read illegal addr in exifscan()
The exifscan() function in Exiftags 1.01 may allocate a buffer that is not long enough, leading to illegal memory access when calling memcmp().
Sample files: crash9, crash22
=================================================================
==251528==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000012 at pc 0x5594a3138426 bp 0x7ffeeade2280 sp 0x7ffeeade1a28
READ of size 6 at 0x602000000012 thread T0
#0 0x5594a3138425 in MemcmpInterceptorCommon(void*, int (*)(void const*, void const*, unsigned long), void const*, void const*, unsigned long) crtstuff.c
#1 0x5594a313894d in memcmp (/work/programs/exiftags/src/exiftags.asan+0xb494d) (BuildId: a1af0030b9f6a6f4)
#2 0x5594a31fd1cf in exifscan /work/programs/exiftags/src/exif.c:839:6
#3 0x5594a31f7f28 in exifparse /work/programs/exiftags/src/exif.c:902:12
#4 0x5594a31f7f28 in doit /work/programs/exiftags/src/exiftags.c:152:7
#5 0x5594a31f6c80 in main /work/programs/exiftags/src/exiftags.c:280:8
#6 0x7fefd07fc6c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#7 0x7fefd07fc784 in __libc_start_main csu/../csu/libc-start.c:360:3
#8 0x5594a311bfd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
0x602000000012 is located 0 bytes after 2-byte region [0x602000000010,0x602000000012)
allocated by thread T0 here:
#0 0x5594a31b6c22 in malloc (/work/programs/exiftags/src/exiftags.asan+0x132c22) (BuildId: a1af0030b9f6a6f4)
#1 0x5594a31f7e85 in doit /work/programs/exiftags/src/exiftags.c:141:30
#2 0x5594a31f6c80 in main /work/programs/exiftags/src/exiftags.c:280:8
SUMMARY: AddressSanitizer: heap-buffer-overflow crtstuff.c in MemcmpInterceptorCommon(void*, int (*)(void const*, void const*, unsigned long), void const*, void const*, unsigned long)
Shadow bytes around the buggy address:
0x601ffffffd80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x601ffffffe00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x601ffffffe80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x601fffffff00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x601fffffff80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x602000000000: fa fa[02]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x602000000080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x602000000100: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x602000000180: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x602000000200: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x602000000280: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==251528==ABORTING
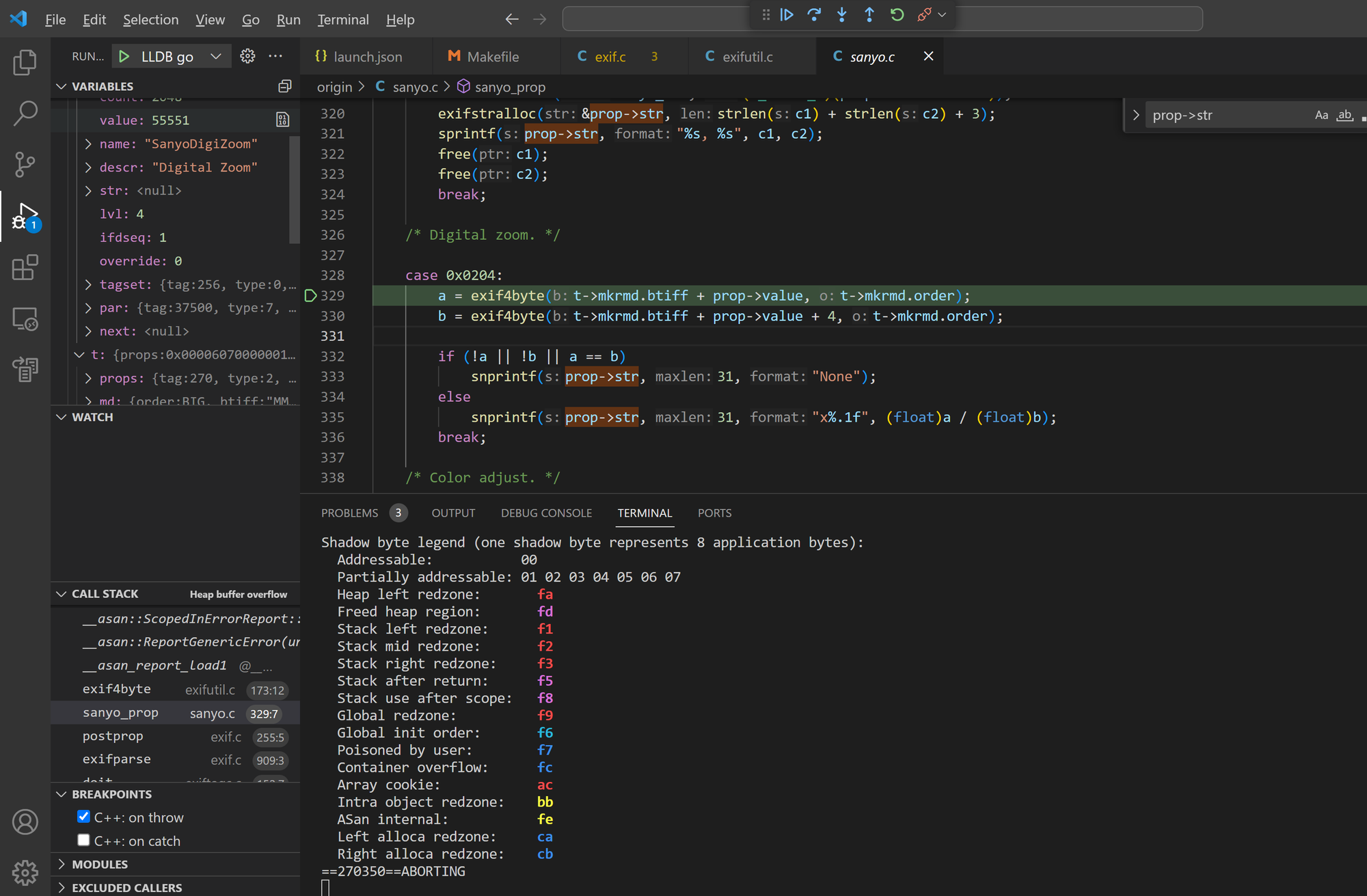
Bug 8 - arbitary memory read in sanyo_prop()
The sanyo_prop() function in Exiftags 1.01 has an offset field overflow issue, leading to arbitrary address reads.
Sample files: crash10, crash18
=================================================================
==244014==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62100000ee05 at pc 0x55e54f09527a bp 0x7ffe0bdfdf90 sp 0x7ffe0bdfdf88
READ of size 1 at 0x62100000ee05 thread T0
#0 0x55e54f095279 in exif4byte /work/programs/exiftags/src/exifutil.c:173:12
#1 0x55e54f0af2e5 in sanyo_prop /work/programs/exiftags/src/sanyo.c:329:7
#2 0x55e54f08876d in postprop /work/programs/exiftags/src/exif.c:255:5
#3 0x55e54f08876d in exifparse /work/programs/exiftags/src/exif.c:909:3
#4 0x55e54f08876d in doit /work/programs/exiftags/src/exiftags.c:152:7
#5 0x55e54f086c80 in main /work/programs/exiftags/src/exiftags.c:280:8
#6 0x7f3a5f68b6c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#7 0x7f3a5f68b784 in __libc_start_main csu/../csu/libc-start.c:360:3
#8 0x55e54efabfd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
Address 0x62100000ee05 is a wild pointer inside of access range of size 0x000000000001.
SUMMARY: AddressSanitizer: heap-buffer-overflow /work/programs/exiftags/src/exifutil.c:173:12 in exif4byte
Shadow bytes around the buggy address:
0x62100000eb80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000ec00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000ec80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000ed00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000ed80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x62100000ee00:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000ee80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000ef00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000ef80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000f000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x62100000f080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==244014==ABORTING
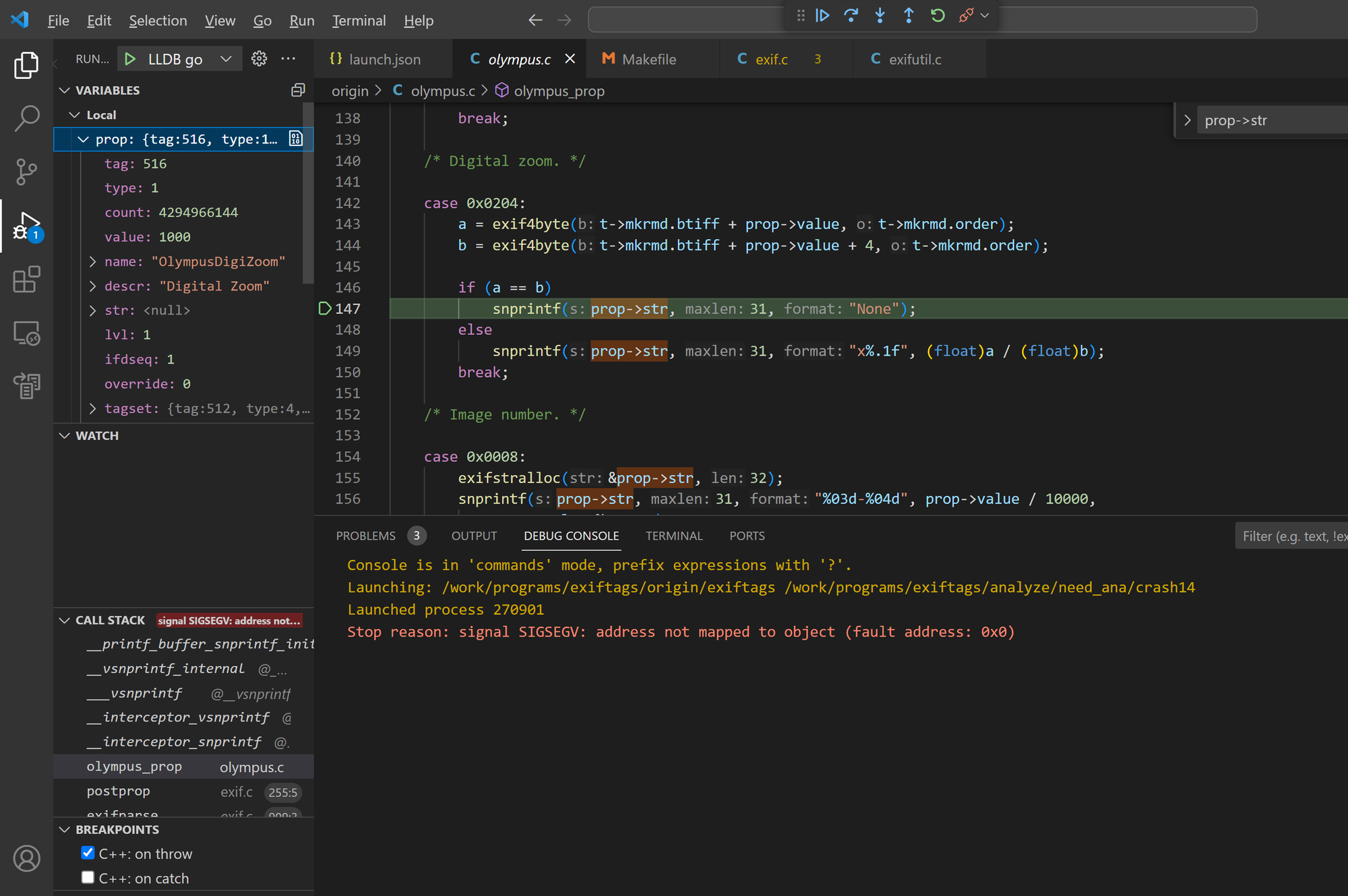
Bug 9 - null pointer dereference in olympus_prop()
The olympus_prop() function in Exiftags 1.01 has a null pointer dereference issue, leading to illegal memory access.
Sample files: crash14
AddressSanitizer:DEADLYSIGNAL
=================================================================
==238165==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f7573e70c78 bp 0x7ffc3ddad490 sp 0x7ffc3ddacc48 T0)
==238165==The signal is caused by a WRITE memory access.
==238165==Hint: address points to the zero page.
#0 0x7f7573e70c78 in __memcpy_avx512_unaligned_erms string/../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:289
#1 0x559c62369c27 in __asan_memcpy (/work/programs/exiftags/src/exiftags.asan+0x131c27) (BuildId: a1af0030b9f6a6f4)
#2 0x559c623ac76d in postprop /work/programs/exiftags/src/exif.c:255:5
#3 0x559c623ac76d in exifparse /work/programs/exiftags/src/exif.c:909:3
#4 0x559c623ac76d in doit /work/programs/exiftags/src/exiftags.c:152:7
#5 0x559c623aac80 in main /work/programs/exiftags/src/exiftags.c:280:8
#6 0x7f7573d2d6c9 in __libc_start_call_main csu/../sysdeps/nptl/libc_start_call_main.h:58:16
#7 0x7f7573d2d784 in __libc_start_main csu/../csu/libc-start.c:360:3
#8 0x559c622cffd0 in _start (/work/programs/exiftags/src/exiftags.asan+0x97fd0) (BuildId: a1af0030b9f6a6f4)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV string/../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:289 in __memcpy_avx512_unaligned_erms
==238165==ABORTING